Problems of counteraction to cybercrime and cyberterrorism in Ukraine
Date: January 02, 2005Source: Computer Crime Research Center
By:
Processes of globalization and development of the modern civilization are described by transition of industrial society to information. Wide introduction of modern information technologies creates new, unique opportunities for more active and efficient development of economy, politics, country, society, social consciousness and a citizen. However, enhancement of technologies leads not only to strengthening of industrial society, but also to introduction of new sources of danger to the society unknown before. The economy and defense of top countries of the world in a growing way depend on normal operation of the global computer networks. Halt of their operation can cause serious sequels; in fact, national and international legal institutes are not ready to counteract adequately to these new threats.
A well-known Russian criminologist, professor Vladimir Luneev in his monograph entitled “Criminality of the Twenty First century” shows dynamic, initiative and creative character of modern criminality; it immediately uses new rising and available areas that are poorly monitored by the government; modern criminals change kinds, forms and ways of their activity depending on the situation, they are not bound by any legal, moral and even technical norms and rules. “Unlike clumsy governmental bodies, criminals can use latest achievements of science and engineering very fast”.
Obtaining undoubted advantages in the use of information systems built on the basis of global computer networks, Ukraine gradually becomes more dependent on their proper functioning as well. This fact pushes us to elaborate new approaches to protect the interests of a personality, society and state in this sphere. The Concept (Bases of the State Policy) of the National Security of Ukraine determines threats to national security and interests of Ukraine; computer crime and cyber terrorism are among them.
After awful by scales and cynicism events of September 2001 in New York and Washington, global community’s attitude became more sharp, their reaction became more conscious, coordinated and consequent. In the recent years various national and worldwide forums raised discussions of terrorism in general, and cyberterrorism in particular, resulting in consultations of specialists of “narrow” separate fields and even roundtables at governmental levels. Documents signed at these meetings create favorable conditions for straight actions directed at counteraction to terrorism.
One of the most serious steps taken to regulate this problem was the adoption of Cybercrime Convention by European Council on 23 November 2001, the first international agreement on juridical and procedural aspects of investigating and prosecuting cybercrimes . It specifies efforts coordinated at the national and international level and directed at preventing illegal intervention into the work of computer systems. The Convention stipulates actions targeted at national and inter-governmental level, directed to prevent unlawful infringement of computer system functions. The Convention divides cybercrimes into four main kinds: hacking of computer systems, fraud, forbidden content (racist websites and child porn content) and breaking copyright laws.
By ways and mechanisms these crimes are specific, have high latency and low exposure levels. There is another descriptive feature of these crimes: these crimes are mostly committed only with the purpose to commit other more gravy crimes, for example theft of money from bank accounts, getting restricted information, counterfeit of money or securities, extortion, illicit production of audio and video materials, espionage.
According to the Ministry of Internal Affairs of Ukraine, 95 cases related to computer crimes were disclosed for the first 6 months of 2004; in 2003 – 122 cases, 2002 – 25 cases and 7 cases for 2001.
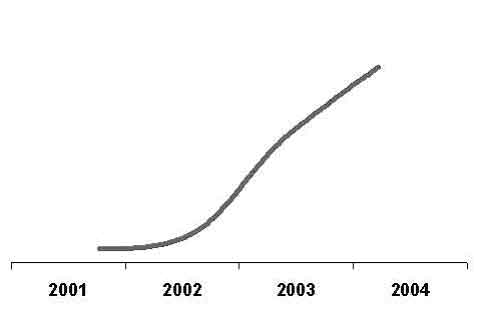
As compared to the data of the Russian police, 4995 cases related to computer crime were opened in 6 months of 2004, 7053 cases in 2003, 3872 cases in 2002 and 1619 in 2001.
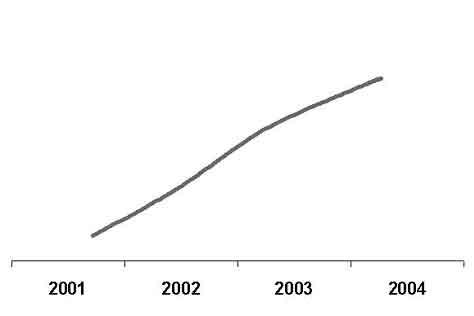
According to Department "K" (a department on fighting high tech crimes), the analysis shows that 16 per-cent of malefactors who acted in the sphere of "computers" were young men below 18 years; 58 per-cent aged between 18 and 25 years, 70 per-cent of these had high or incomplete high education. The main share of crimes relates to illegal access to information and use of malicious software. It was noted that officers of the department were quite successful in their struggle against such crimes.
According to Ukraine Antivirus Center, the losses caused by cyber attacks for 6 months 2004 made about 45 million Euro. It is 30 per cent more than for 6 months 2003.
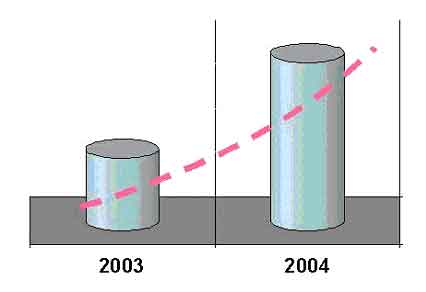
The biggest damage per one PC falls to the share of the average business, where companies have numbers of computers and minimum information security budgets. Most of huge Ukrainian companies began to pay more attention to the antivirus protection after the last year's epidemics. These efforts helped them to minimize their losses this year.
Besides, attacks related to home users significantly increased for this period. For instance, more than 90 per-cent of Ukrtelecom Internet Service Provider users were affected by virus attacks for the first six months of 2004 .
The Ukrainian Antivirus Center experts note that the increase in the quantity of personal computers, bandwidths' capacity leads to ever-increasing scaled virus epidemics and accordingly losses caused by them.
Ukrainian experts and criminologists are greatly interested in statistics from the USA brought by the FBI annual report. The report pointed that overall financial losses totalled from 494 survey respondents were $141,496,560, it is down significantly from 530 respondents reporting $201,797,340 last year .
The amount of successful attacks on computer systems is constantly decreasing starting from 2001. Only 53 per-cent of interviewed companies noted that their companies incurred damages due to unauthorized access to their computer systems this year. It is the lowest showing since 1999. The number of companies that haven’t encountered any unauthorized access problems rose up to 35 per-cent, while 11 per-cent do not know whether they have or haven’t experienced unauthorized access problems and this makes up the lowest mark since 1999 again.
Taking into account social danger represented by cyberterrorism, it is necessary to outline displays of high-tech terrorism, especially computer terrorism or cyberterrorism. This kind of terrorism causes special anxiety of experts due to high vulnerability of computer systems in the sphere of critical infrastructure management (transport, nuclear power stations, water supply and energy) that are connected to the Internet.
A threat of terrorism on the Internet has become more scaled than appeared; opportunities of cyberterrorism became more sophisticated along with the total spread of the Internet. It is a serious threat, similar to nuclear, bacteriological and chemical weapons. It is still not understood and studied well. The worldwide experience in fighting against cyber-terrorism shows the vulnerability of every state. As computer-terrorism has no frontiers, cyber-terrorists target information systems everywhere.
D. Malyshenko in his article entitled “Counteraction to Cyberterrorism – Important Task of the Present-Day Society and State”, said that computer terrorism should be observed as
- one of kinds of unlawful access to computer information stored on a separate computer or a network of computers;
- with the purpose to modify, delete this information or to learn it,
- causing situation where functioning of the given computer or a network goes beyond established normal mode of operation;
- it creates danger to people’s lives, material damage or other socially dangerous sequels. The main purposes of the given above actions are: social security violation, bringing fright to the population, armed conflict provocation, international complication or influence on decision making, commitment or non-commitment an action by state or local authorities, officials, or attracting attention of public to certain political, religious or other judgement of a terrorist and also threat of committing mentioned actions on the same purpose.
Therein the most probable is the manifestation of activities of international terrorist groups directed to the detriment of efficient activities of international organizations acting in restless regions of the world according to the authorities delegated by the UN.
Cyber attacks and special advanced skills of hackers are widely utilized and sponsored at governmental levels, though as any special operation, it is performed without publicity.
Hackers of Pakistan and India are involved in a real jihad for Kashmir. According to Hindustan Times news, Pakistani hackers defaced 477 Indian websites – 270 of them in April, 2003 alone – against the 288 sites they hacked in all of 2002. Some of these websites belonged to Indian governmental bodies. In turn, Indian hackers calling themselves “Indian Snakes” spread Yaha worm as “cyber revenge”. The virus aimed at performing DDoS attacks on some Pakistani sources, including ISPs, website of Karachi Stock Exchange and governmental sites.
In North...
 Add comment
Add comment
 Email to a Friend
Email to a Friend
 Next
Next